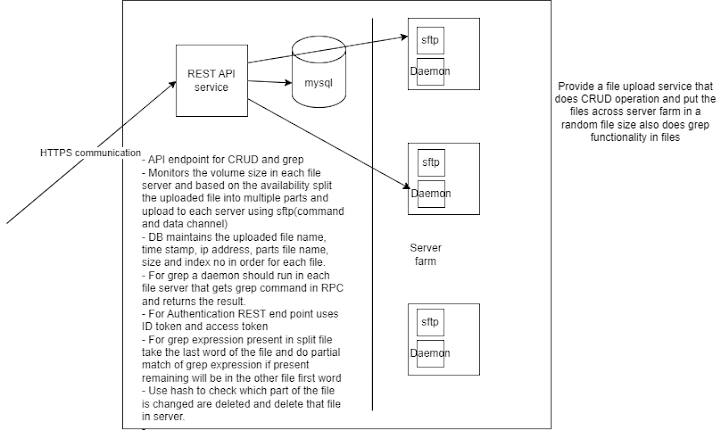
Class Decorator practical uses - Part 2
Last part we have seen about function decorator and how to use it to add extensions to existing functions. We have seen how decorator are useful, today we can see about how to use class based decorator which will provide extension functionalities to existing functions. How we can configure a class decorator during creation so that we can configure a decorator for our need. Lets get started with code. def func ( msg ): print ( f "Hai programmer we got this message { msg } for you " ) if __name__ == "__main__" : func ( "Hello Developer" ) Now for adding a class decorator we need to understand two things one is how the constructor is invoked for a class and how functors is used while invoking an object of a class. While creating a instance of the class like below. class MyDecorator : def __init__ ( self , func ): obj = MyDecorator ( func ) Now we created an instance passing function as a parameter object. Since function is a first clas...